When you browse the web, you often reveal more information about yourself than you intended. At the most basic level, your IP address will reveal which country you are based in. However, at more advanced level, the people who host the website that you are viewing can associate your personal data with your IP address. If connection to a website is un-encrypted, than anyone can do it, not just the intended recipients of the data.
Your data is especially vulnerable when you are out and about being connected to wireless hotspots. In this situation, everybody else who is connected to the same hotspot can see all the data that you are sending and receiving or, if connection is encrypted, at least what sites you are visiting.
There are various ways of keeping your web browsing private and today we will summarize 3 most popular of them.
Proxies
Proxy is a server which sends web requests and receives web responses on your behalf. When you use a proxy over a secure connection, all parts of your original request get encrypted, so nobody who would intercept the message would be able to determine what you are sending and where you are sending it, as the destination IP address would belong to the proxy server and not the actual website.
When the request reaches the proxy server, it substitutes your IP address with its own and passes the message to its intended destination. Then the reverse process takes place to transfer the response back to you.
The target server will have no idea what your IP address is, so this method will not only keep your connection private, but will also enable you to browse any content blocked in your country via a proxy server based in another country.
This method, however, has its own dangers. There are many proxies out there that are ran by hackers, so all your personal data that goes through them will be available to them. Some of them also trick you into installing malicious programs on your device. Therefore you should use only those proxies that you absolutely trust.
Another minor downside of this method is that it is slower than a direct connection, as each message has to go through an intermediate point and there is some extra computation involved. However, with ever-increasing network speed, this should not be an issue most of the time.
VPN
VPN, which stands for Virtual Private Network, has originally been created to enable employees of an enterprise to work remotely by connecting to the inner network of the enterprise from the outside. Being on VPN is just like being in the office. Just like with proxies, there is a server within the enterprise network that communicates with the web on your behalf.
VPNs are more secure than proxies, as each packet that gets sent over the internet is encapsulated within another packet and is completely hidden from the view. This is why communicating via VPN is often known as tunneling.
Unlike proxies, VPNs are not very easy to use. In most of the cases, you would need to install a software on your device and apply some very precise configuration. You would also need a network to connect to, which needs to be set up to enable tunneling.
However, there are some examples of publicly accessible VPNs, some of which are free. The same precaution should be taken as with proxies when using those, as you can’t always know who hosts them and what intentions do they have.
Tor
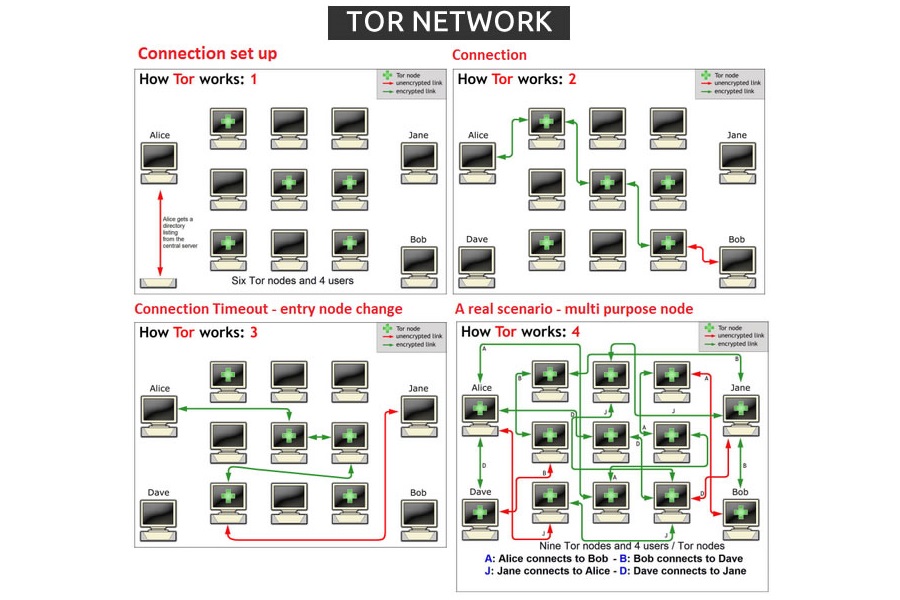
Tor stands for The Onion Router and is one of the most reliable (if not the single most reliable) ways of interacting with the web anonymously. The reference to onion is not random.
Tor works by applying several encapsulation layers to your web request, which goes through a series of relay servers before reaching its intended destination. Each of the relay servers in the dedicated Tor network strips one of encrypted encapsulation layers from the package before passing it to the next server, which is just like peeling layers of an onion. The final server sends your package to its intended destination.
Before your request even enters the network, it is stripped of all non-essential identifying information, such as your operating system. As your message is very strongly encrypted, the only things that are readable in the package are the IP address of the previous server in the relay and the IP address of the next server in the relay.
There is no way of telling where the package is going, unless it is intercepted once it left the exit node, i.e. the final server in the relay. Even then, it would not be possible to determine where did the package originate from. So, unlike a standard proxy, your package is safe even if one of the relay servers is compromised.
To make the system even more secure, the path through the server relay is random. This means that even within a single session different web requests will take different routes. Servers are added to the network on voluntary basis; you can even add your computer as a relay server if you wish so (although I would not recommend it).
Tor requires a dedicated browser, which is based on Mozilla with a lot of stuff added. This is free to download, as the software is open-source, which means that a dedicated worldwide community of developers work collaboratively to improve it. The official Android version of the browser is known as Orbot.